Capcom says last year's ransomware attack exploited an 'old VPN' that had been kept online due to Covid-19
In November 2020, Capcom announced that it had been hit by a ransomware attack: Hackers had infiltrated the company's servers, encrypted data on its devices, and claimed to have downloaded over 1TB of data. According to one malware researcher at the time, the hackers also left behind a demand for $11 million in Bitcoin in exchange for the encryption key.
In its final report on the matter, released today, Capcom denied that any specific ransom demand had been made, and said that it was never actually in contact with the hackers.
The report includes a timeline of events, from the initial detection of potential problems to now, and a slight reduction in the number of individual accounts confirmed as compromised: 15,640, rather than the 16,415 reported in January. That number is primarily made up of current and former employees but also includes a few thousand "business partners," which Capcom clarified does not include customers.
There’s also an explanation of how attackers were able to break into Capcom's systems in the first place. The company said its worldwide networks had been recently upgraded prior to the attack, but an "older backup VPN" remained in use in North America in order to help it manage the increased load arising from the Covid-19 pandemic. And, like the proverbial exhaust port on an impregnable battle station, the attackers were able to exploit it to get inside and do damage.
"Some devices were compromised at both the Company's US and Japanese offices through the affected old VPN device at the Company's North American subsidiary, leading to the theft of information," Capcom explained. "While the Company had existing perimeter security measures in place and, as explained below, was in the processes of adopting defensive measures such as a SOC [Security Operation Center] service and EDR [Endpoint Detection and Response], the Company had been forced to prioritize infrastructure improvements necessitated by the spread of COVID-19. As a result, the use of these measures was still in the process of being verified (not yet implemented) at the time this matter took place."
Here's a handy diagram:
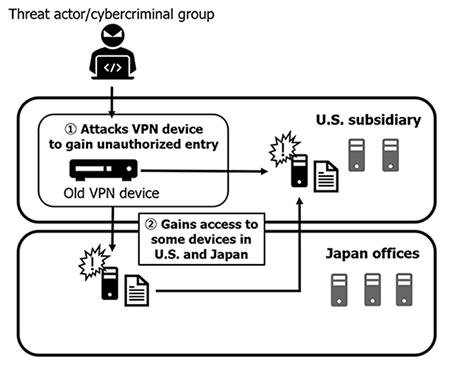
That old device is now gone, and Capcom has implemented a range of technical and organization measures aimed at reducing the likelihood of something like this happening again in the future. External companies have conducted a review and "cleaning" of Capcom's networks and implemented new monitoring and early warning systems, while Capcom itself has launched new internal divisions, including an Information Technology Security Oversight Committee and Information Technology Surveillance Section, to stay on top of potential future threats.
The good news, as far as it goes, is that none of the compromised data included credit card information, and the attack did not impact any parts of Capcom's systems related to purchasing or playing games. "It remains safe for Capcom customers or others to connect to the internet to play or purchase the company's games online,” Capcom said.
Interestingly, it also clarified that it was never actually in contact with the attackers, and had not received the reported $11 million ransom demand.
"While it is true that the threat actor behind this attack left a message file on the devices that were infected with ransomware containing instructions to contact the threat actor to negotiate, there was no mention of a ransom amount in this file," it wrote. "As explained in previous announcements, Capcom consulted with law enforcement and determined to not engage the threat actor in negotiations; the Company in fact took no steps to make contact … and as such Capcom is not aware of any ransom demand amounts."
Capcom is reaching out to people whose information was compromised, and provided contact information for anyone who wants to inquire about the breach: Through the Capcom customer service website in North America at www.capcom.com/support; via email to feedback@capcom.com for customers in Europe, the Middle East, and Africa; and by phone for those in Japan at 0120-400161. It also repeated its "deepest apologies" to customers impacted by the attack, and promised to "endeavor to further strengthen its management structure while coordinating with the relevant organizations to pursue its legal options regarding criminal acts."